Client Affairs
August Big Read: The Dark Side Of The Dark Web

Sometimes explainers are necessary to describe terms that crop up but which few may fully understand. One is "the dark web." Financial crimes consultancy Themis takes a deep dive into the covert marketplace, following the influence of cryptocurrencies and how crime is being tackled there.
The origins of the “dark web” lie with a US Department of Defense-led attempt to create an anonymized and encrypted network for spies and military personnel; it now refers to an unregulated part of the internet accessed via specific browsers. It originally needed to be a form of internet that was isolated from ordinary users and yet offered sufficient practicality for agents in the field.
Some of the program’s core researchers also realized its potential to offer unchallenged civilian privacy and a place for human rights activists to protect their freedom of speech - the very same anonymity that the US DoD demanded could potentially also allow individuals trapped under oppressive regimes to voice their opinions and to access wider media outlets.
While access to a truly anonymous server free from authoritarian powers sounds like an activist’s dream, the reality has proved far more sinister. The dark web has facilitated the movement and sale of many illegal and harmful goods and services — for example drugs, weapons, stolen identities — not to mention human trafficking.
The scale of this traffic is striking:
Dark web activity has increased by 300 per cent in the last 3
years.
- Over 30 per cent of North Americans access the dark web
regularly.
- In 2020, around 133,000 logins and emails from Fortune 1000
C-suite executives were available on the dark web.
- More than 22 billion new records were added to the dark web in
2020.
The dark web is primarily accessible via the Tor network or The Onion Router (TOR). The name originates from the idea that the many layers of an onion denote the many levels of security and encryption on the dark web. TOR serves as a portal, with a collection of websites that are inaccessible to regular servers. It can be downloaded free from clear net browsers like Google. Also in keeping with the theme of anonymity, the primary form of payment on the dark web is cryptocurrency, a largely untraceable form of money where transactions are recorded but in a decentralized system using cryptography.
The dark web provides users with an easy avenue for carrying out illegal activities. From the privacy of one’s own home, any individual who understands how to peel back those onion layers can access a range of sinister material and substances or even commission a contract killing.
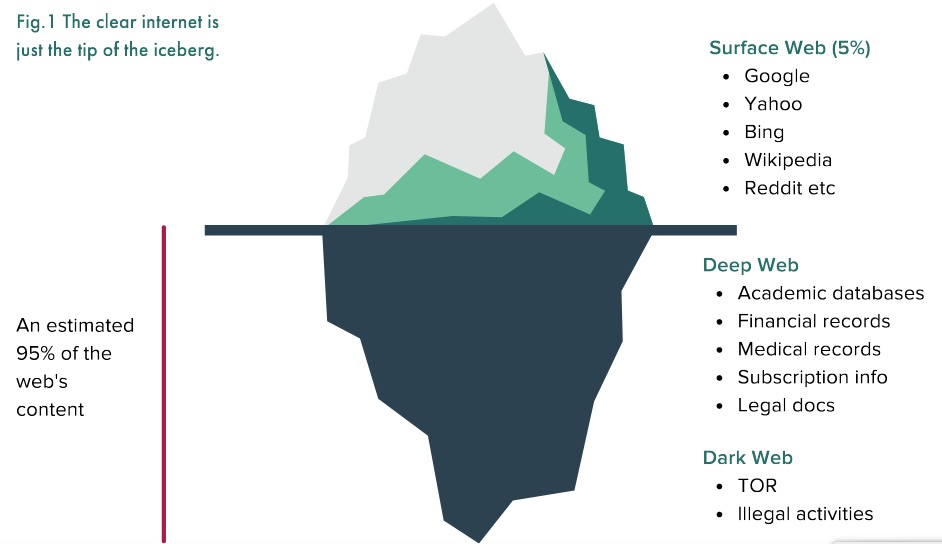
The dark web 101
The dark web is best imagined if we split the internet into three
parts: the “clear/surface” web relates to some of the most common
parts of the internet which are easily accessed from most
standard browsers and computers. When we conduct a search on
Google, like most search engines, it navigates the request
through the surface web which accesses public pages and logs our
requests.
Then we have the “deep” web — this relates to pages that the search engines are not able to index, for example, those with passwords or personal information, such as online banking or social media. The difference is that the deep web is only accessible to registered users, while the surface web has no restrictions.
Finally we have the “dark” web — an area of the internet inaccessible via traditional search methods and computers, where pages and information are explicitly designed to be concealed from mainline search engines and casual users. Of the roughly 2 billion websites on the clear and deep webs, the dark net represents 5 per cent of these, of which only a few are available at any given moment.
When someone uses the clear or deep web, their computer’s IP (internet protocol) address will communicate with the website and request access to the page for content. The information is then returned but a record of the visit will have been stored by the webpage. IP addresses are location-tied and so enable websites and regulators to see where the user is accessing the information.
This allows tracking services such as Google to monitor traffic levels and user data to create profiles which are then used by internet service providers and advertising agencies to generate ads or for website maintenance. The Tor browser prevents such tracking by allowing individuals to access information with encrypted routing technology without being traced; and its search engine cannot index any of the passing data.
Besides offering access to dark net sites, it allows users to travel the clear and deep websites anonymously via the encryption of personal and location-based data. Those who help to maintain Tor have described its activities as “using a twisty, hard-to-follow route in order to throw off somebody who is tailing you — and then periodically erasing your footprints”.
So who uses Tor to access the dark web?
As of September 2019, there were over 65,000 URLs registered with
the TLD (Top Level Domain) “onion” on the Tor browser.
Cyber-security firm Hyperion Gray cataloged about 10 per cent of
these websites and found that the most common pages were chat and
discussion forums, image hosting sites, and marketplaces —
offering a suggestion, at least, that it is a foundation for free
speech societies.
In fact, many major clear and deep web sites such as Facebook, the New York Times, and the CIA, have an online presence on the dark web and Tor browser, which could serve as a portal for those wishing to communicate with these organizations anonymously or whistleblow without a backlash. More individually, there are also people who fear that their personal information can be exploited on the open web and use Tor as a privacy tool.
However, a technology that facilitates such privacy also presents an ideal way for criminals to conduct their business. A survey by King’s College London found that out of more than 2,500 live dark web pages surveyed over five weeks in 2015, at least 57 per cent hosted extremely illicit material. As with face-to-face deals, everything and anything can be found online: recreational and pharmaceutical drugs, firearms, personal and financial data, malware-for-rent, human organs, and even trafficked humans make up some of the many thousands of listings that appear on the dark web.
Many vendors offer a mix of these services, and the competitive nature of the e-commerce market often ensures a high street shop-level of customer service. E-marketplaces encourage their customers to leave positive reviews for their services and goods and make every effort to replace or troubleshoot defective software or merchandise.
This data is then used to create “vendor trust level” rankings, which allow individuals to choose their vendor based on quality, delivery time, or percentage success, and the sellers then capture more of the market share as a result. Some even use automated delivery systems for software and digital products — they deliver the goods immediately after the individual’s purchase and allow for around-the-clock service.
The dark in “dark web”: how is it exploited by
criminals?
Second only to drugs, fraudulent and corrupted data is the most
popular listing on dark web markets. It consists primarily of
personal and corporate information, often extracted not for
personal use, but for its potential for monetization. Personal
data such as medical records, bank/card details (and the software
used to extract such products) and other sensitive material can
be found on the dark web. Businesses’ commercial details are also
commonly found.
Hackers target research data (new drugs and therapies for example), trade secrets and formulas (proprietary inventions or recipes), blueprints and security schematics for banks and buildings, and often intelligence reports (investigations, budgets, etc) and insider communication (such as a firm’s next M&A bid). These are then either released to the public for open access and abuse, or more often used as blackmail against the individual or organization.
Continual streams of these breaches fill the dark web marketplace with ‘produce’. Lists of emails, usernames, passwords and social security numbers can be found, which are then used to create profiles of individuals either to be exposed, used as ransom or even hijacked as a money/information dump. Credit cards, payment and banking information or payment processor accounts are either sold for their surface value, or sometimes used in money laundering schemes.
They can act as a first access point for the laundering of illicit proceeds, where money is deposited as cash into these accounts and quickly transferred to subsequent encrypted accounts to avoid tracing.
Examples of what is for sale on the dark
web:
Login credentials to a $50,000 Bank of America account: $500 on
the dark web;
$3,000 in counterfeit $20 bills: $600 on the dark web;
Seven prepaid $2,500 debit cards: $500 on the dark web [express
shipping included];
A lifetime Netflix premium account: $6 on the dark web.
Fraud forums and shops sell these compromised payment and credit card details, which in turn can be filtered by categories such as issuing bank or expiry date. The forums also offer opportunities for individuals to request specific financial and personal data of a particular victim or to organize partnerships in money laundering for illicit profits.
One of the most successful examples of these financial data marketplaces is Joker’s Stash. The platform for trading stolen credit cards and identity data was founded in 2014 by an individual calling themself “JokerStash,” who posted encrypted messages in both English and Russian. The site had a presence on the dark web and a surface web domain. it took until December 2020 for Interpol and the FBI to shut down the accessible site.
More surprising, Joker’s Stash is a rare example of a profitable and established dark web page that chose to bow out on its own terms. In January 2021, the operation said it was shutting down for good within a month, fulfilling that promise. The site charged users activation fees for the accounts and took percentage commissions from the sales, all paid in bitcoin.
A suggested reason for the closure was the soaring price of the cryptocurrency over the last few years. Rising from little more than $300 per coin in 2014, it hit $49,000 by the time Joker Stash’s closed. Blockchain analytics and compliance firm Elliptic estimates that Joker’s Stash amassed more than $1 billion in profits from fees and the radical growth of cryptocurrencies value over the years.
Crypto influence
The use of cryptocurrencies on the dark web exposes individuals
and businesses to financial crime, including money laundering.
Early dark web transactions relied on PayPal and Western Union to
pay for goods and services. These payment systems involved a
certain level of user interaction which could be used by law
enforcement agencies.
But crypto’s anonymity has largely changed that. Its use by criminal organizations has been a concern for regulators for some time, promting calls from US Treasury Secretary Janet Yellen and European Central Bank President Christine Lagarde, and others for much stricter regulation to combat abuse.
One area where crypto has proved particularly effective is among hackers demanding ransoms. In 2020, at least $350 million was paid to ransomware gangs, including DarkSide, the hackers responsible for the 2021 Colonial Pipeline breach.
As the spending of crimminal proceeds can raise suspicions and lead to arrest, individuals often need to launder money. The United Nations estimates that the amount of money laundered in one year globally is between $1.6 trillion and $4 trillion (or 2 to 5 per cent of global GDP). While the dark web makes up a relatively small part of the overall number, the increase in online banking and integration of technology into our lives could lead to a rapid escalation.
Russia’s largest dark web marketplace Hydra has a built-in crypto ecosystem that makes the use and laundering of crypto relatively easy. When the virtual money needs to be exchanged for real cash, an individual might seek a ‘Treasure Man’, often found as a listing-for-hire on e-markets such as Hydra, who will organize the transaction via prepaid cards, coin cleaning or physical exchanges.
Commenting on Hydra’s Uber-like system of drop spots, Dr Tom Robinson, scientist and co-founder of Elliptic, said: “They will literally leave bundles of cash somewhere for you to pick up. They bury it underground or hide it behind a bush, and they’ll tell you the coordinates. There is a whole profession.”
However, each crypto transaction leaves a marker on an immutable blockchain which in turn can be exposed by forensic groups, e.g. Chainalysis, to show the passage of the money and its ties to a specific wallet. In total, in 2020, some $5 billion in funds was received by illicit entities, and those illicit entities sent $5 billion on to other entities, all of which needed to be cleaned.
Methods include:
Chain hopping — rapidly exchanging one coin for
another in order to lose online footprints, or simply using coins
with even greater privacy features such as Monero.
Coin cleaning — mixing laundered crypto with other funds of legitimate crypto before redistributing them. Although it is theoretically possible to then un-jumble them, it takes time and significant resources.
Privacy wallets — an obfuscation tool used to move around 12 per cent of all laundered bitcoin in 2020, which allows coin mixing and has extra privacy measures built in.
What is being done to tackle crime on the dark
web?
Governments in Turkey, Ethiopia, China, Venezuela and elsewhere
have attempted to block access to Tor and thus to the dark web.
However, the move has often been driven by internet censorship
and surveillance aims rather than necessarily curbing crime on
the dark web. Constructive ways in which governments and law
enforcement bodies can genuinely counter exploitation of the dark
web are by information sharing, increasing their technical
understanding of the cryptography aspects, and regulating
cryptocurrency transactions.
For instance, in 2018 to 2019, Interpol and Europol brought together agencies and information across 19 countries to assemble a list of 247 high-value targets related to the dark web. By working together to understand dark web operations better, members of this combined force made arrests and were able to shut down over 50 illicit dark web sites, including two of the largest drug trading pages, Wall Street Market and Valhalla.
Another success was the FBI’s takedown of “Silk Road 2.0." Silk Road was a dark web market that regularly served over 100,000 users globally buying and selling drugs. Silk Road 1.0 was removed in 2013 but its replacement soon popped up and continued operations. However, a combined task force of the FBI and the European Cybercrime Centre managed to decrypt large amounts of information and arrested Blake Benthall, who is said to have covertly owned and operated the site.
Exact details of the techniques used are not, surprisingly, available, but various explanations have been suggested, including double agents placed within the site’s employee bank; vulnerable nodes (Tor access points) being compromised by the FBI to unscramble traffic; or simply that the site’s security and encryption was less effective than first thought.
Nevertheless, this case offers hope that well-established sites on the dark web being used for nefarious means can be taken down through governments and law enforcement agenies uniting and sharing information to evolve detection methods.
Crypto asset regulation
At the 2018 G20 Summit, there were calls for reforms to consider
crypto assets and relevant Know Your Customer (KYC) and
anti-money laundering (AML) schemes, which led to a flurry of
regulatory initiatives.
The EU tackled the crypto asset sector regulation via its 5th Anti-Money Laundering Directive (5AMLD), which is the bloc’s first AML directive to cover digital wallet providers and crypto asset/cryptocurrency exchanges. EU member states were required to bring these businesses under AML-related regulatory supervision by January 2020. EU regulation of the industry is likely to go much further.
In September 2020, the European Commission published its proposed Regulation on Markets in Crypto-Assets (MiCA) which, if passed, would expand the range of crypto assets covered by EU legislation and introduce a shared, harmonized European framework for the currencies. The European Commission expects the MiCA to become law within the next four years.
Similarly, there have been suggested amendments under EU law that would require providers of crypto wallets and exchange services to collect the details of the parties involved in relevant deals. These would include any known addresses, dates of birth, account numbers, and names of recipients, and would effectively prevent holding anonymous wallets.
Following the UK’s adoption of the 5AMLD in January last year, crypto asset exchanges and custodian wallet providers are now covered by the UK Money Laundering Regulations (MLRs) and subject to regulatory oversight. Non-compliant providers are liable to fines of up to €200,000.
The Financial Conduct Authority is the AML and counter terrorist financing watchdog for businesses carrying out crypto asset activities in the UK. UK-based commercial exchanges and custodian wallet providers must register with the FCA specifically for AML supervision before undertaking relevant crypto asset business, even if they are already FCA-authorized in another respect.
In addition to these developments, there is an increasing number of services run by forensic firms that can notify individual exchanges of suspicious activity based on their intelligence and findings, and blacklisted crypto wallets. There is also talk of creating blacklists of particular crypto wallets linked to suspicious activity and money laundering, While these would require open sharing of information across national bodies, in July this year, Kemba Walden, assistant general counsel at Microsoft’s Digital Crimes Unit, suggested that action on "policy initiatives” is needed now, in light of the increasing presence of crypto in modern life.
A 2020 report by Elliptic, suggested that between 2011 and 2019, some of the larger crypto exchanges allegedly helped cash out between 60 and 80 per cent of bitcoin trades from known criminal activity. With the introduction of stronger regulation and the increased awareness of dark web threats, many of the exchanges have strengthened their AML and KYC processes and the percentage share of illicit cash-outs reduced to 45. Enhanced regulations have encouraged some criminals to turn to unlicensed exchanges (less likely to ask for KYC information, operating in less stringent jurisdictions), but these have significant drawbacks in terms of limited liquidity and transaction size.
What can businesses do to protect themselves most
effectively against criminals on the dark web?
1. Understand the dark web and how it works — this will
remove the novelty and scope for employees to be confused or
deceived by it. With greater knowledge of these security risks
and methods, it is more likely that any irregularity will be
spotted.
2. Engage in regular employee training — in a 2018
industry report conducted by the information security company
Shred-it, 47 per cent of business leaders said that employee
negligence was responsible for their data breaches. Businesses
ought to engage in regular employee training about information
security and evolving cyberthreats.
3. Keep work hardware and software separate from employees’
personal devices — try to use encryption software and
firewalls wherever possible.
4. Mitigate potential risk from dark web threats and data
breaches — keep updated records of financial information and
how it is stored and accessed. Firms should limit access to
important data exclusively to those who need it, and protect it
with multi-layered passwords and firewalls.
What is the future of the dark web?
Although a source of privacy and freedom for many, its anonymity
represents a useful avenue for criminals to exploit. As
with “offline” criminal activity, unfortunately there will always
be a demand for illicit products and services and so a need for a
supplier. Furthermore, the dark web continues to change rapidly
and criminals are finding creative ways around any progress that
is made to shed light on the dark web’s extreme untraceability.
The evolving nature of warfare poses a particularly worrying potential opportunity for dark web exploitation. In the future, wars will be even more heavily reliant on technological disruption and cyber warfare rather than traditional hand-to-hand combat, and governments ought to consider countermeasures and monitoring capabilities such as dark web-focused threat intelligence, in order to adequately counter the threat. This is in addition to deepening current international information-sharing initiatives and steps being taken by law enforcement to limit and disrupt any physical aspects of trade conducted via the dark web, including packaging, shipment and cash transactions.
Themis does not advise its members to try accessing the dark web at home. One of the risks of doing so is that you leave yourself open to ransom from criminal organizations that may threaten to expose your activities or personal and organizational information.